Token Trust & Traceability WG April 2025 Call
https://codimd.web.cern.ch/lu033dy1S4WTefJlj2zDMg
# TTT April 2025 Meeting
**Attending:** Linda, Patrick, Maarten, Jens, Mischa, Marcus, DaveD
**Apologies:** DaveK
Chair:Matt
---
## Actions, recap from last time.
No outstanding actions.
CHEP Paper accepted.
Would like to reach out to Jens, was on the to do for this meeting.
Jens is here today.
Collated previous risk assessment documents:
Linda's EGEE assessment: https://edms.cern.ch/ui/file/1039446/1/EGEE-III-SCG-TEC-1039446-SecurityRisk-v0_9.pdf
Acompanying spreadsheet: https://edms.cern.ch/file/1039446/1/OverallGridSecurityRA-fulldata-rev250309.xls
Romain's report: https://cern.ch/rwartel/security_teg/WLCG%20Risk%20Assessment.pdf
## Discussion, recent meetings
- Token Lifetime meeting tomorrow (the finale?)
- TIIME token risk assessment session.
- Any other news from TIIME? Outcomes from FIM4R?
Run through Jens' notes from TIIME:
2 sessions on token translation, can we use translation as replacement for proxied introspection
- sketches a diagram
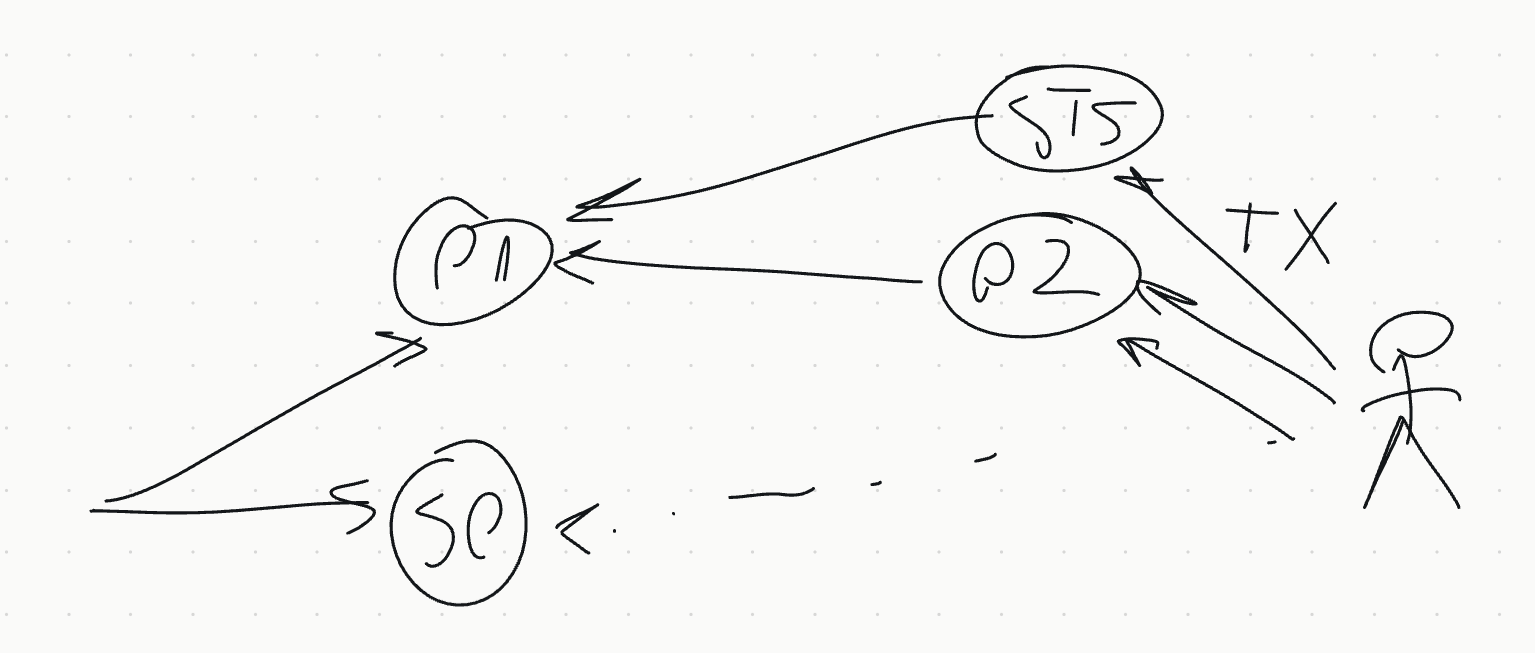
STS: Secure Token Service (Leif)
WIMSE protocol suggested for this.
User doesn't specifically trust P1.
Keycloak (according to documentation) that in the latest release can do token exchange.
MS- two options, since two infrastructures: use token from infra1 in infra2 or vice versa. Proxied token introspection is one, solution here is the other, which is better depends on the use-case. The main thing is go for simplicity, and work out both two scenarios.
ML- note that this is not a use case for WLCG.
JJ- Had example of US and European colabb (Globus in US, and EGI checkin in Europe).
ML- still good to have background information to keep aware of the bigger picture.
Aim to have difficulties "hidden" from users (and hopefully sites)
MS - All complexities should be in the AS (for both scenarios).
JJ does another sketch, for when AAI (INDIGO IAM) publishes entitlements.
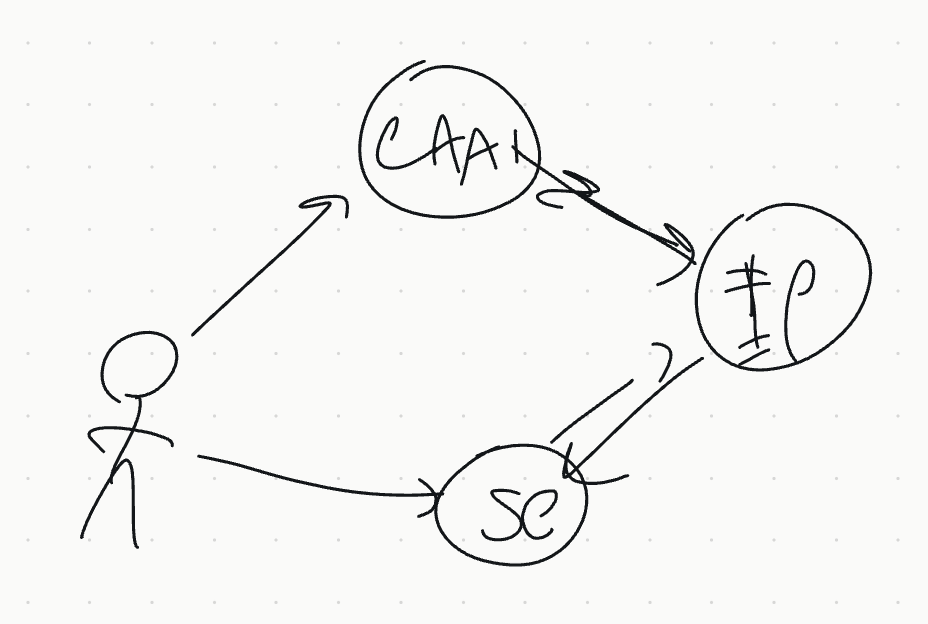
Question on how you minimise attributes (especially if member of more then one community)
Need a way of telling community proxy to just give what I need. Assert minimal attributes.
ML - "solved" by using multiple clients, but this isn't nice. But there's an IAM issue with this.
- In fact, an issue was just opened about it.
Notes that IAM is in (partial) production for data movement. Still pushing this.
Notes discussion at WLCG workshop next week. Also reminds that some of this is set by practical limits and experience.
SKA concerns, ML notes FTS will support more then one model.
Talks about levels of assurance, and discovery service "hints" to ensure that enough assurance is had.
No existing mechanisms solves this problem of hinting at assurance.
Can I ask for a specific ACR (Authentication Context R...)? Yes you can.
If need a lot of **AND**s can add ACRs, but usual logic is an **OR**.
Can we get this done with just one user interaction?
ML - this functionality doesn't exist today, marked as an area for developement in AARC
This could be something that hits WLCG users at some point.
JJ - Hannah asked a question at TIIME if a user needed to log out of proxy? Not a great user flow, especially if automatic.
One last doodle on a user doing multiple actions at a site, for SKA working on a single proxy for a site that forwards the connection.
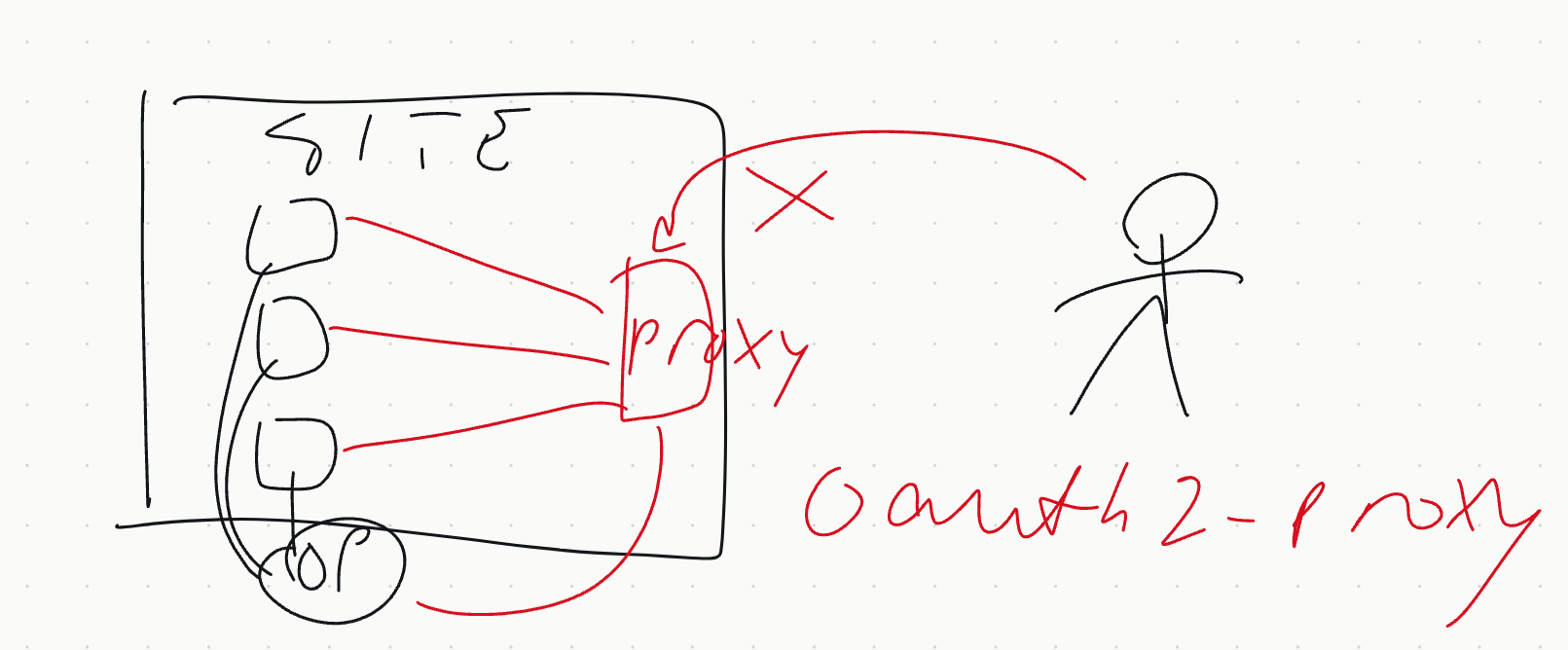
disadvantage is that every service looks like it's from the proxy.
in practice used oauth2-proxy
Can encrypt, but can't use openid anymore so must have trust within site.
ML - WLCG has offline validation, so no callouts
within purvue of this group, as we don't have CRLs or Argus-equivilent (at the moment).
These come with increased complexity, and the issues that brings.
Notes issues seen with online validation.
Banning at the token issuer level. Experiments are partners in security incident handling.
Probably adopt a ban first, ask questions later approach if given a user.
Mitigation from giving tokens as little power as possible. Should be factored in to discussions/assessments.
ML - need within this WG to document approaches that work.
JJ - there is a privacy issue with banning users and letting over sites know.
Also how will SAML transition to openid-federation? -- a big question!
### TIIME Links
https://docs.google.com/document/d/1TIcP-V8WqEHvgD2if4vjn9XaPwuf-1ukPrChsuJq08Y/edit?tab=t.0
https://docs.google.com/document/d/1AcOmhxIUTKkaIaxiFH8UtD88AECAN1pBrdiq3ESPODQ/edit?tab=t.0#heading=h.xfxuay1g5bs2
### Actions, AOB, Next Meeting
New meeting discuss risk assessments.
Next meeting 27th May.
